WinBox in RoMON mode necessitates the agent is the latest Model to have the ability to hook up with the latest Edition routers.
For MikroTik routers, It really is essential to arrange passwords. We recommend utilizing a password generator Software to produce robust passwords that meet the next criteria:
Notice: Log in into the router utilizing the new qualifications to validate that the username and password are performing the right way.
You’ve also bought a blog, which can be absolutely free. General, This is a legitimate multiverse of adult content material like no other internet site.
Now, the sole downside is Mamacitas has much less videos than other Internet websites on this record – close to a thousand.
To permit Classification look at, ideal mouse click on the merchandise record and in the popup menu decide Show Classes
include chain=enter in-interface=ether1 action=take protocol=tcp port=8291 remark="make it possible for Winbox"; include chain=input in-interface=ether1 motion=settle for protocol=tcp port=22 remark="permit SSH"; incorporate chain=enter in-interface=ether1 motion=fall remark="block everything else";
Neighbor discovery will clearly show also products that aren't suitable with WinBox, like Cisco routers or almost every other machine that employs CDP https://www.winboxgame.com.my/ (Cisco Discovery Protocol). If you might test to connect with a SwOS product, then https://winboxmalay.com/pages/winbox-register the relationship will likely be recognized via a Internet browser
You will discover animated VR and AR strip golf equipment it is possible to take a look at, AND even now Engage in several of the porn videos in the history.
Click on the + button to open up a fresh dialog box. You may both enter a personalized bridge https://www.winbox-mobile.com/ title or retain the default bridge1, then simply click Alright to move forward;
A further advantage of this type of setup is always that NATed purchasers powering the router are not directly connected to Read more the Internet, this way supplemental security from attacks from outdoors mainly isn't needed.
The technological storage or obtain is strictly necessary for the legitimate objective of enabling the use of a specific assistance explicitly requested with the subscriber or person, or for the sole function of finishing up the transmission of a communication about an electronic communications community. Preferences Tastes
The franchise is made up of 10s of sister internet sites, and all have a pretty identical Read more consumer facial area, so it’s uncomplicated to change backwards and forwards between them.
Choose in form the next fall-down box. "in" means that filter will Look at if DST deal with benefit is in variety of the desired network.
 Ariana Richards Then & Now!
Ariana Richards Then & Now! Kelly McGillis Then & Now!
Kelly McGillis Then & Now! Robert Downey Jr. Then & Now!
Robert Downey Jr. Then & Now! Elin Nordegren Then & Now!
Elin Nordegren Then & Now!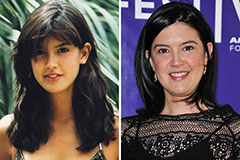 Phoebe Cates Then & Now!
Phoebe Cates Then & Now!